Blogs & Articles
 Blogs
Blogs Why PTaaS is a Game Changer for Your Cybersecurity?
In the ever-evolving world of cybersecurity, the traditional methods of vulnerability assessment often fall short of meeting the dynamic demands...
 Blogs
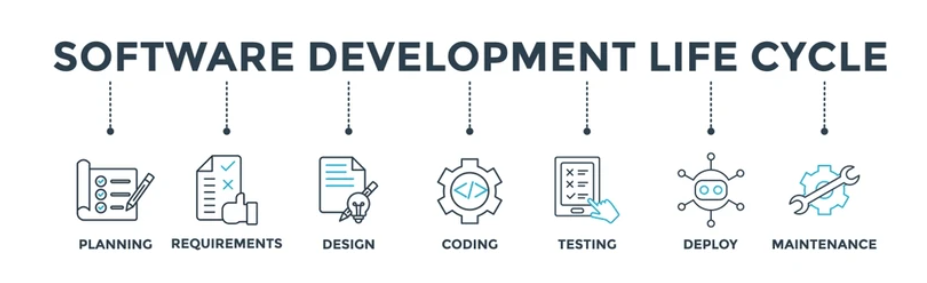
Blogs Secure SDLC: A Deep Dive into Building Secure Software
In today's interconnected world, software vulnerabilities are a goldmine for cybercriminals. Data breaches, ransomware attacks, and system disruptions are just...
 Blogs
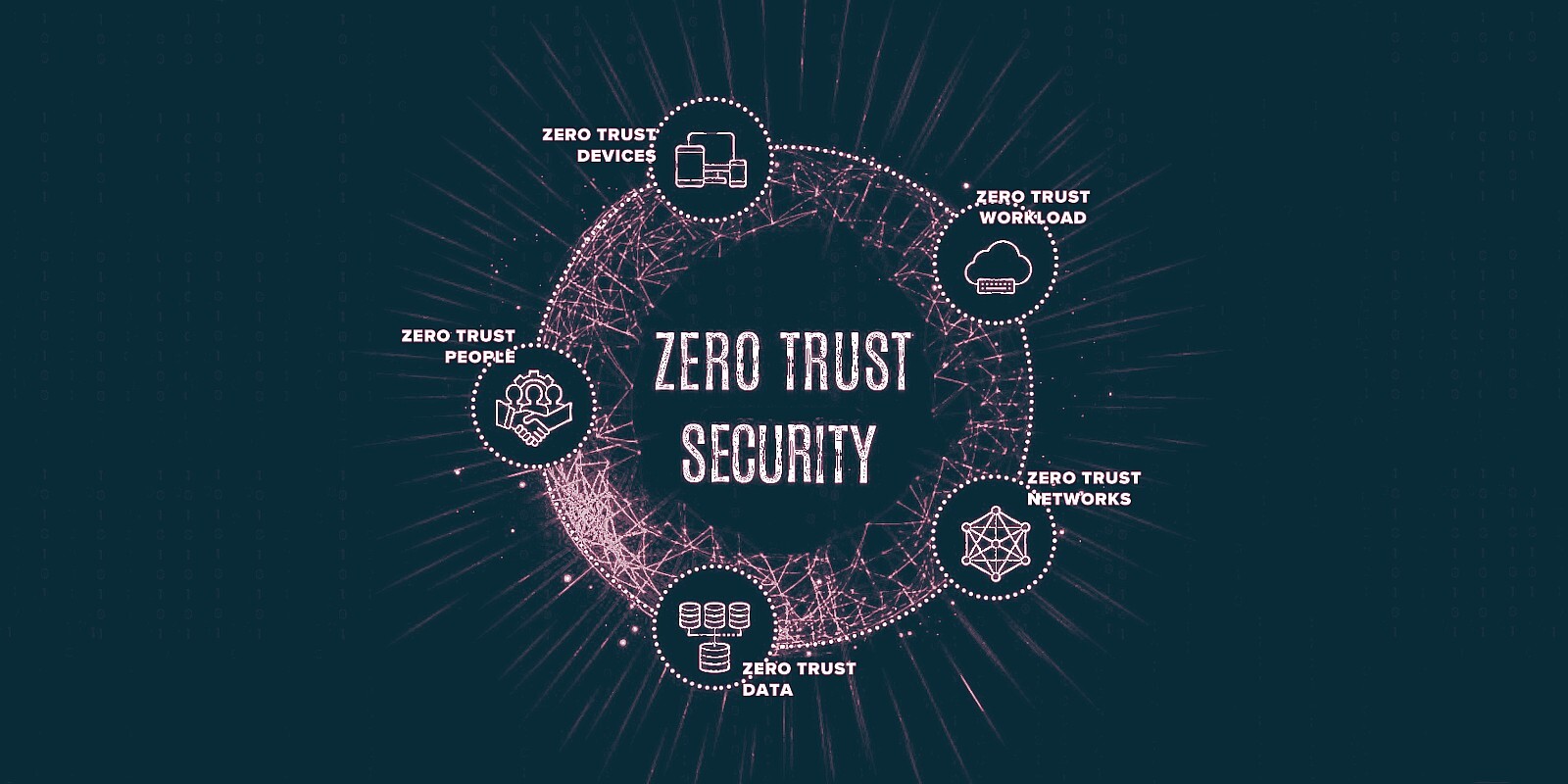
Blogs How to Implement a Zero Trust Security Model in Your Organization
As businesses evolve and adopt digital-first strategies, the traditional perimeter-based security model is becoming obsolete. With the rise of remote...
 Blogs
Blogs Top 5 Cybersecurity Trends to Watch in 2024
Cybersecurity is an ever-evolving landscape, with new threats and challenges emerging as technology advances. Businesses, governments, and individuals are under...
 Blogs
Blogs The Importance of Penetration Testing as a Service (PTaaS) in Modern Cybersecurity
In today’s digital age, businesses of all sizes face an increasing number of cyber threats. From data breaches to ransomware...