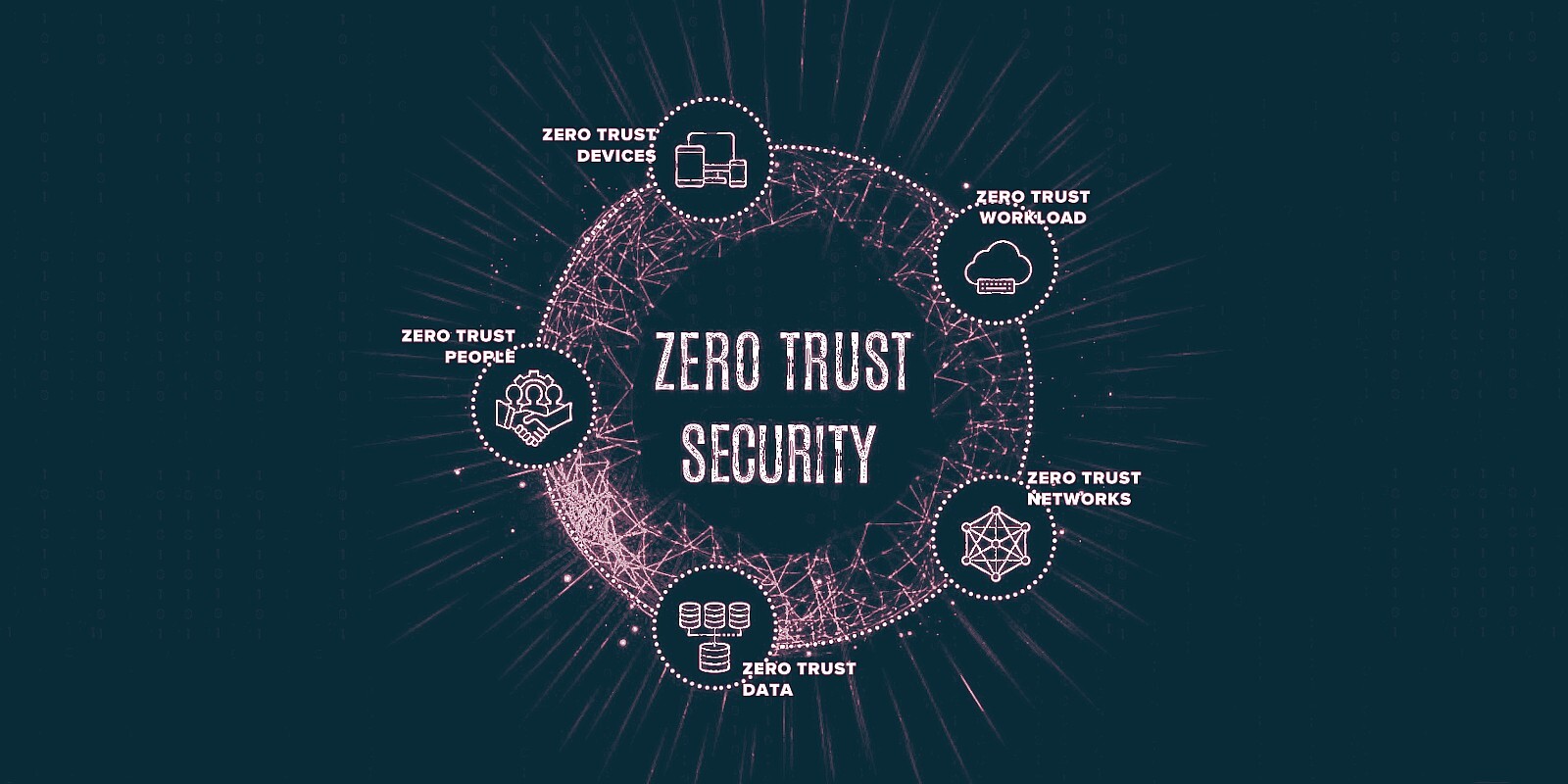
How to Implement a Zero Trust Security Model in Your Organization
As businesses evolve and adopt digital-first strategies, the traditional perimeter-based security model is becoming obsolete. With the rise of remote work, cloud computing, and mobile devices, organizations are exposed to more vulnerabilities than ever before. A Zero Trust security model addresses these challenges by ensuring that no entity—whether inside or outside the network—is trusted by […]